
On October 6, 2014, Tether (then Realcoin) launched USDT, one of the first fiat-backed stablecoins, celebrated at the time as a way to “digitize the dollar” onchain and give crypto a stable medium of exchange.
Up to that point, most cryptocurrencies faced extreme volatility. They offered programmability and decentralization, but their price swings made them impractical for everyday transactions. Stablecoins, on the other hand, proved ideal for this use case.
The idea was simple. For every USDT in circulation, there should be a dollar (or equivalent) in reserve. This made the cryptocurrency more stable (in theory) and more intuitive for users.
Today, stablecoin growth has been exponential. They’re now central to decentralized finance, powering payments, lending, and global transfers. Still, with that growth comes risk. Smart contracts and wallets behind them are frequent targets for exploits, and attackers continue to probe for flaws that let them drain funds or bypass safeguards.
This article explains why stablecoins matter, how they’re built, and why stablecoin security has to go deeper than just smart contract design. Then it shows how Turnkey protects stablecoin transactions with policies enforced at the signing layer, helping mitigate attacks before they ever reach user funds.
Valuing the stablecoin market
Since 2014, Stablecoins have grown tremendously. As of mid-2025, the total stablecoin market cap, or the value of all stablecoins in circulation, exceeded $250.3 billion, with U.S. dollar-backed stablecoins accounting for roughly $245.5 billion of that total.
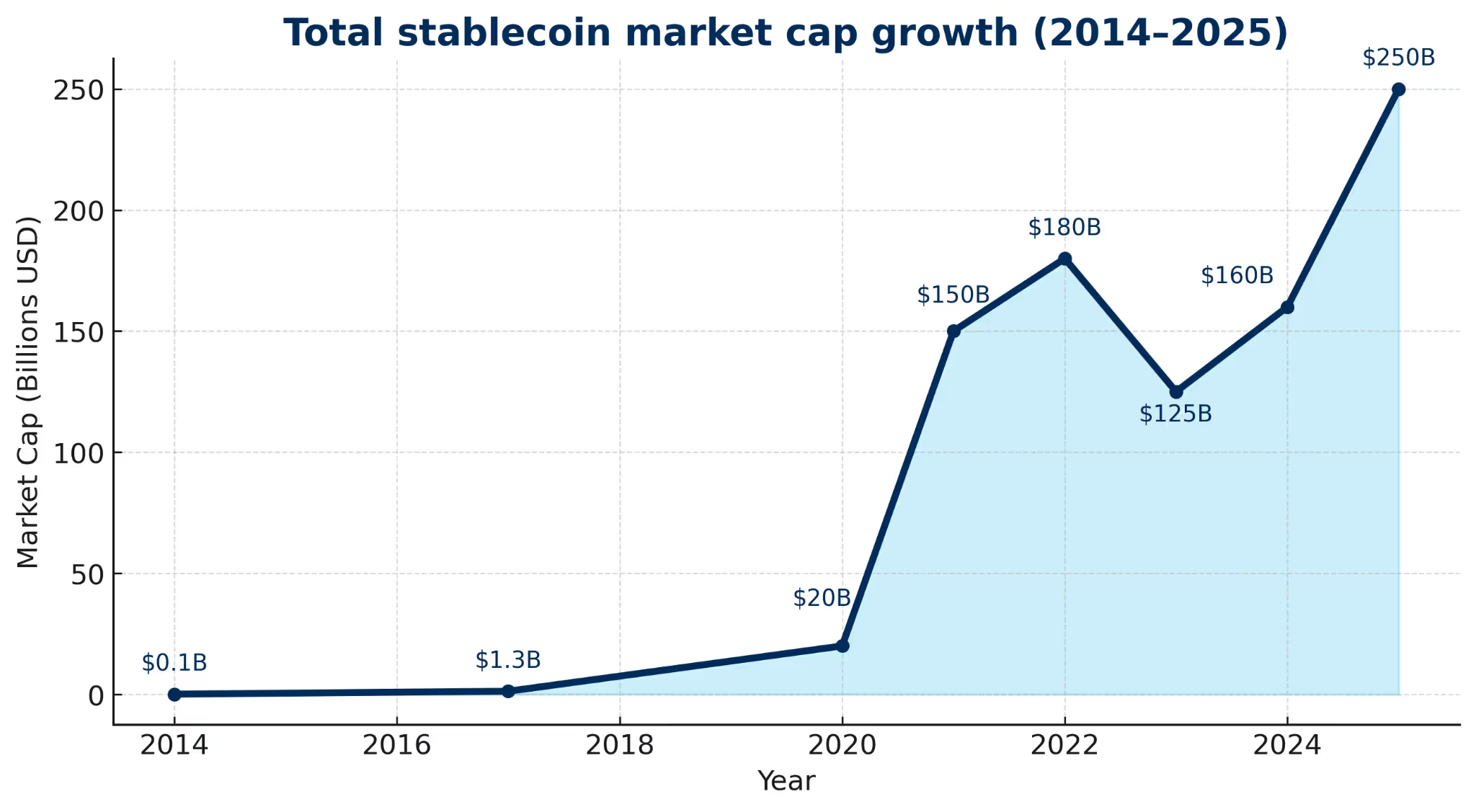
Between January 2023 and February 2025, $94.2 billion in stablecoin payments were settled, driven heavily by B2B transfers and card-linked payments. Today’s predictions are projecting even more growth in the years to come. McKinsey, for example, says we could see stablecoin daily transaction volume at $250 billion in daily activity within a few years.
Currently, most of that volume still comes from trading, but payment use is growing each year. This trajectory shows that stablecoins are not just a niche financial instrument but a building block for the next phase of digital commerce.
The difference between stablecoins and other cryptocurrencies
Unlike many cryptocurrencies, stablecoins are not primarily speculative assets. They are tools for settlement, remittances, and onchain commerce.
This utility comes with different security requirements. Stablecoins run on smart contracts that must be executed safely, without exposing users to policy failures or malicious changes.
For developers, understanding how these systems are built is critical, as it reveals the mechanisms that keep stablecoins functional and safe to use. At their core, most stablecoins need to be pegged to something that is stable in value, and they need code to help keep this peg consistent.
How stablecoins work
Most stablecoins combine a smart contract with an asset or pool of assets that back the token and define how it can be issued or redeemed. Stablecoin stability is achieved through a combination of blockchain smart contracts, reserves, and sometimes algorithmic controls.
A smart contract, code on a blockchain that runs automatically once predefined conditions are met, defines how any stablecoin will operate. It specifies the peg (for example, $1 per token) and enforces the conditions for minting and redeeming tokens.
When new tokens are issued, the contract requires collateral or reserves to back them. This ensures that each stablecoin maintains a predictable value tied to the underlying asset.
There are three main ways this peg is maintained:
- Custodied reserves: Centralized stablecoins such as USDC and USDT are backed by real-world assets held off-chain by banks or custodians. For every token issued, there is a dollar or dollar-equivalent asset stored in reserve.
- Collateralized contracts: Decentralized stablecoins are backed entirely onchain by crypto collateral locked inside smart contracts. Users deposit crypto assets (e.g., ETH) into a contract, which then issues stablecoins pegged to the dollar. If collateral values fall, the contract automatically liquidates positions to maintain the peg.
- Algorithmic controls: Some stablecoins use algorithmic supply adjustments. Smart contracts expand or contract the token supply based on market demand, attempting to keep the price near the peg without full backing by reserves.
Trust assumptions differ here. Fiat-backed coins shift risk to centralized custodians, while crypto-collateralized models push responsibility to contract logic and collateral management.
In all of these, though, the smart contracts that mint, redeem, and enforce collateral rules are prime targets for exploits. A single bug or oracle failure can cascade into billions of dollars of losses.
Why Turnkey believes stablecoin security should start at the signing layer
When a wallet transacts with stablecoins it interacts with its smart contract, and every one of these transactions ultimately depends on a signature to authorize the movement of funds. This makes signing one of the most critical checkpoints in the system.
Even if a contract is sound and collateral rules are enforced, the signature is the final gatekeeper. Protecting it means protecting every downstream action that depends on it.
Policy as a defense mechanism
Policies define how wallets can be used. Without them, every signature would be valid in any context, leaving no protection against mistakes or malicious transfers. Embedding policies at the signing layer ensures assets move only under predefined rules.
Some policies that developers could opt to include:
- Spending limits: Cap transaction size or total daily/weekly volume.
- Destination controls: Restrict transfers to approved addresses or block risky ones.
- Time-based rules: Allow transactions only within certain time windows.
- Multi-party approvals: Require multiple signatures before large or sensitive transfers.
- Transaction type restrictions: Permit only specific contract calls (e.g., payments, not swaps).
- Asset-specific limits: Set different rules for stablecoins vs. volatile tokens.
- Geographic or compliance filters: Enforce restrictions based on jurisdiction or regulatory rules.
- Rate-limiting: Prevent rapid sequences of transactions that could indicate an exploit.
These signature policies are vital for keeping digital transactions safe, but they must also be secured. If they live outside a trusted environment, attackers can compromise the external system, disable controls, and bend policies to their advantage.
This creates a critical weak point, one that could drain assets even without direct access to the wallet’s private keys.
Turnkey vs. other stablecoin security models
Unfortunately, many companies that offer wallet infrastructure place their policy logic in external systems that lack the protections needed to keep those policies safe. This separation introduces a structural weakness: even if the signing keys are secured, the rules that govern how they are used remain exposed.
Often this happens because it is simpler to build policies outside of a secure environment, or because certain models, such as MPC, are practical only for a narrow set of operations inside their key-protection layer.
As a result, policies are pushed outward, where they become easier targets for attackers. This “policy outside the perimeter” model leaves stablecoin workflows vulnerable at their most critical point, the moment a signature authorizes value to move.
Turnkey takes a different approach. With Turnkey, both keys and policies live inside a Trusted Execution Environment (TEE), where hardware isolation guarantees that neither can be tampered with.
This means the rules governing stablecoin transactions are inseparable from the act of signing itself. By uniting policy enforcement and signing within the TEE environment, Turnkey eliminates a weak link that attackers often exploit.
For developers, this model reduces risk while strengthening trust. Every transaction is evaluated against rules that cannot be bypassed, whether that means enforcing spending limits, requiring multiple approvals, or restricting destinations.
For users, it means interacting with stablecoin applications with the assurance that every payment is controlled by policies that hold firm under attack.
Turnkey keeps stablecoins secure
Stablecoins are too valuable to rely on partial security models. By enforcing policies directly at the signing layer, Turnkey offers a path to bulletproof stablecoin infrastructure.
For web3 developers, that means stronger protection, fewer risks, and the confidence to scale applications on top of the stablecoin economy. And for users, it ensures that the “digital dollars” they depend on for payments, savings, and commerce remain as trustworthy as the systems they are meant to replace.
If you’re interested in an in-depth security model that goes beyond protecting customer keys, one that safeguards policies, workflows, and every step where assets could be at risk, learn more about how Turnkey can help you build secure stablecoin infrastructure. Sign up for Turnkey and start building.
Related articles
.png)
Turnkey for Agent Identity (ERC-8004, SIWA, and empowering trustless AI)
Turnkey is helping to operationalize ERC-8004 by supporting the infrastructure needed for agents to register identities and operate securely across services.
.png)
20+ skills and MCP servers bridging AI and blockchain development
Here we highlight twenty plus MCP servers and skills for developers to explore.




